When I set out to write this post, I thought to myself: I really hope no one ends up reading it. Because if you’ve landed here out of necessity, your business has been hacked. And you’re in a bad spot.
Therefore—I’m going to skip the preamble and get right to it. Keep reading for your list of the six immediate steps to take after you think you’ve become a cyberattack victim.
If you’re not here out of necessity: I recommend reading the last section (on preventing a cyberattack) thoroughly, so you never need to land on this page again.
How to know if you’ve been hacked
The words “YOU’VE BEEN HACKED” rarely display themselves so readily to actual cyberattack victims. Instead, look for the following signs, which could indicate that your device has been compromised:
- Your internet browser’s homepage is different than usual.
- Your computer keeps crashing and is running unusually slow.
- Unknown programs start up when you turn on your computer or connect to the internet.
- Your email, passwords or other account settings have been changed.
- Emails are being sent from your account.
- Posts or friend requests are being initiated (not by you).

What to do if you’ve been hacked
If you suspect you’ve been hacked, it’s important to remain calm and take immediate action.
Here’s what to do first:
No. 1: Notify
If you have an internal IT department, reach out to them immediately. If you use an outside agency, contact them before touching anything else on your device.
Hopefully, your IT support (whether internal or external) will reach out to you to let you know that they suspect you’ve been compromised. A well-equipped technical team has systems monitored 24/7/365 for tracking suspicious activity, so they should have known something was awry before you did.
They’ll want to isolate your system to prevent it from impacting other devices connected to your network, so make sure you’re in sync with them before doing anything else.
No. 2: Identify
In order to limit the damage and prevent the attack from happening again, you must identify exactly what happened.
- Did you open what you thought was a legitimate email attachment?
- Did someone maybe crack a not-so-cryptic password?
- Did you open a link that was sent to you in a text message?
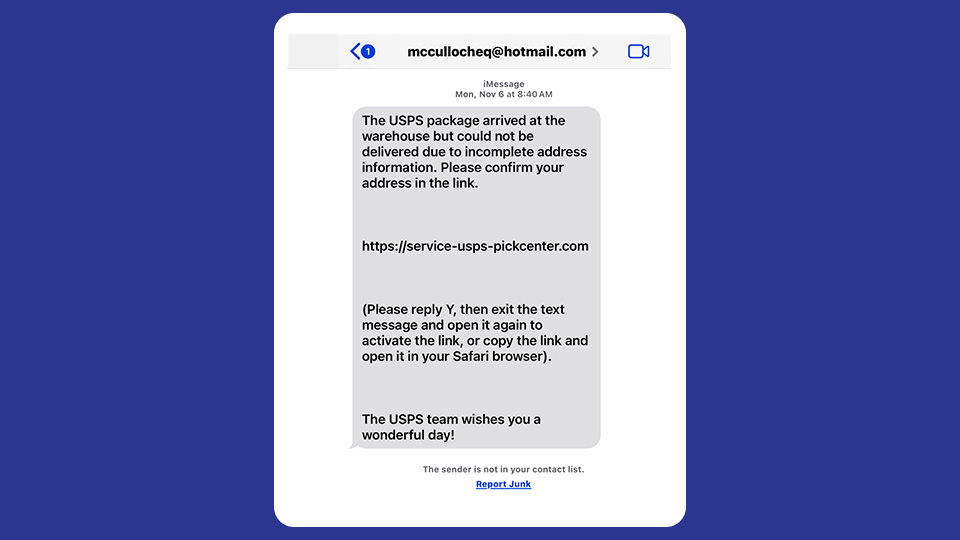
Everyone makes mistakes. And these days, it’s getting more difficult to recognize a bad actor. Don’t be too hard on yourself if you do fall victim to a cyberattack. The most important thing is to figure out what may have happened so you can stop it from happening again.
Also—it’s not on you necessarily to figure out what happened. Your cybersecurity provider will be able to help you find out how the attacker gained access to your system.
No. 3: Contain
Again, your IT team will tell you exactly what you need to do to prevent the attack from impacting other systems—but most likely, they’ll tell you to do this:
- Disconnect your system from the internet.
- Shut down your device.
- Do not attempt to use your device until directed by IT.
No. 4: Assess
Once all is “well” (your system is repaired, and you’ve been given the green light to start working again), it’s time to assess the damage.
- Was it just your system that was impacted?
- Were you a victim of BEC (business email compromise)?
- If yes: Were malware-containing emails sent out from your email address to customers, clients or colleagues?
- Did you lose access to data? Was any of your data deleted?
- If yes: Are you able to restore your backed-up data? (Did you have a backup plan in place?)
No. 5: Report
A cyberattack is a crime and it must be reported to:
- The authorities: Contact your local police department and the FBI to file a report.
- Your cyber insurance provider: If you have cyber insurance—and you 100% should—contact your insurer as soon as possible.
- Cybersecurity and Infrastructure Security Agency (CISA): Organizations are encouraged to report unusual cyberactivity and cyber incidents to report@cisa.gov or 888.282.0870 within 72 hours of the event. See cisa.gov/report for more details.
10 key elements to share when reporting cyber incidents to CISA
- Incident date and time
- Incident location
- Observed activity
- Detailed narrative of event
- Number of people or systems affected
- Impacted company name
- Point of contact details
- Severity of the event
- Critical infrastructure sector
- Informed parties
Source: cisa.gov
No. 6: Inform
“All 50 states, the District of Columbia, Guam, Puerto Rico and the Virgin Islands have security breach notification laws that require businesses or governments to notify consumers or citizens if their personal information is breached.” NCSL.org
The exact legal requirements for notification depend on your type of business, the state you conduct your business in and the type of information you handle.
However, when it comes to personally identifiable information (PII), you must notify impacted parties that their information may have been compromised, regardless of which state or territory you live in.
According to the Federal Trade Commission’s (FTC) “Data breach response: A guide for business,” a business that’s experienced a data breach should:
- Notify the affected businesses. If you think credit card or bank account numbers have been stolen, notify the institution that maintains the accounts so they can monitor for fraudulent activity.
- Tell any impacted party that their information may have been compromised. The quicker you do that, the sooner they’ll be able to change their passwords, monitor their credit activity, etc.
We suggest reading the FTC’s webpage on data breach response thoroughly for more information.
In addition to data breach next steps, they offer a model letter that can be used to send to impacted parties.
How to prevent a cyberattack
We’ve written many, many posts on this very subject. If you’re in a crunch, though, and just need the gist, the cyberattack prevention rules are threefold:
No. 1: Use a cybersecurity provider
A cybersecurity provider will be able to help you avoid a cyberattack with:
- 24/7 device monitoring and threat remediation
- Continuous intrusion monitoring
- Multi-layered firewalls
- Multiple layers of malware detection
- Multifactor authentication
- Proactive support

No. 2: Have a backup plan in place
Backups ensure that if accidental loss or deletion occurs, you’re able to restore whatever data was lost and get back to work.
If your data is compromised in an attack—and some ransomware hacker won’t give it back to you without payment—you won’t have to fork up anything if you have a good backup system in place.
And it just makes good sense!
There are software-specific solutions like Rewind Backups for QuickBooks® Online, and there are full backup solutions that replicate all your hosted app data. Whatever you choose, ensure it backs up every data point that’s critical to your business and that it’s easy to restore.
No 3: Get cybersecurity training
The best, most effective way to prevent a cyberattack is through training. We’re inundated constantly with malicious links; new threats emerge daily that could cause irreparable damage to our finances or reputation.
The only way to stay on top of it is by keeping yourself informed.
When researching the best security awareness training programs, look for those offering:
- Ongoing training (not just “one and done” classes!).
- Simulated phishing to test your course comprehension.
- Full management by a vetted, experienced party. (The last thing you need is another responsibility, right?)
- Training plus other benefits, like 24/7/365 threat remediation should the worst occur.
Security (and then some)
I get it: Security is a lot. It’s a lot for one business to manage themselves—and it becomes even more of a pain if you think you’ve become a cyberattack victim.
And if you do become a cyberattack victim, it’s even worse.
That’s why products like Rightworks Managed Security exist.
Managed Security = Security and then some
Rightworks Managed Security doesn’t just include cyberattack prevention technologies like enterprise-grade endpoint detection and response, ongoing security awareness training and 24/7 monitoring. It also includes what you wouldn’t necessarily expect, like on-demand access to granular backups and tailored-to-your-business phishing simulations.
For more information on Managed Security, contact one of our experts here.
And to become more cyber-savvy, subscribe to our blog below.



