As you know, the Securities and Exchange Commission (SEC) deals with publicly traded companies. So, why should you pay attention to new SEC accounting cybersecurity rules? If you have clients with shares on a stock exchange, the new rules affect you directly. But even if you don’t, they’re worth exploring.
Why? Because what is SEC policy today could easily become a broader policy in the future. If that happens, all accounting firms will need to be ready to document the material effects of a cyberattack on a client. Also, firms must closely monitor who has access to information—and who doesn’t.
New SEC accounting cybersecurity rules include a four-day reporting deadline
The new policy seems simple, but it really isn’t. The accounting cybersecurity rules, adopted in July, require SEC registrants—public companies—that have suffered a cyberattack to report the material impact of the attack within four days of determining what that impact is. The rules also require companies to describe their processes for avoiding cyberattacks and assess the risk they face from cyberattacks.
Here’s a basic breakdown. First of all, publicly traded companies do not have to report a cyberattack four days after it occurs. That would be nearly impossible, as many attacks go undetected for weeks or months. They have four days to report the impact of the attack once they’ve determined what the impact is.
Of course, determining the impact of an attack could take weeks or months after the company discovers and recovers from the attack. But the SEC’s message is one of accountability and punctuality, even if the Commission might find the four-day policy difficult to enforce. Companies aren’t going to be able to hide the damage done by cyberattacks or sit on potentially damaging information for months or years. That’s the idea, anyway.
SEC accounting cybersecurity rules require process descriptions
The rule about disclosing cybersecurity processes will be of particular importance and interest to accounting firms that work with public companies. SEC registrants now must “describe their processes, if any, for assessing, identifying, and managing material risks from cybersecurity threats,” according to the Commission.
That will almost assuredly include companies describing how they deal with accounting firms and other outside contractors. If your firm works with clients that trade on stock exchanges, you’ll need to work with those clients to describe accounting cybersecurity processes. But even if you don’t, the SEC’s action is worth your attention.
What happens with big companies tends to trickle down to smaller ones as veterans of larger businesses move to or start smaller operations. Many smaller businesses take their cues from their larger counterparts, anyway. And with cybersecurity constantly in the news, individuals are going to want to know what kind of protection you’re providing for them, too. Plus, the four-day rule could lead some of your clients to ask for more comprehensive reporting and faster response times.
How accounting firms should respond to new accounting cybersecurity rules
So, even if the SEC’s new rules don’t affect you directly, they should give you a reason to evaluate your own security situation and those of your clients. The four-day rule is a good test. Ask yourself:
- Could you work with a client to determine the damage caused by a cyberattack on the client’s business?
- How long would it take?
- How would you bill for the work?
- Could you even take on that job?
- What if it was your firm that suffered the attack?
You need to be able to answer all of these questions if you can’t already.
In any case, you should be able to describe your accounting cybersecurity setup whenever anyone asks about it, whether it’s a government agency or a client. If you can’t do that relatively quickly and easily, your defenses might be inadequate or incomplete. The best way to avoid having to document a cyberattack is never to suffer one in the first place.
The easiest way to deal with security is to have experts take care of it for you. Run your critical applications and store your client data in the cloud. Or consider outsourcing your whole IT operation altogether. Either way, you’ll know where you stand with cybersecurity, and you’ll know your clients’ data is safe.
Encourage your clients to communicate with you through a secure online environment in the cloud or through secure email protected by your cloud provider’s managed security service. Standard email, portable data devices and even paper pose significant security risks. Communication online also boosts efficiency and reduces response time.
Comply with accounting cybersecurity rules by monitoring who can see data
There are other actions you should consider as well. Companies of all sizes today deal with massive amounts of data that are growing all the time. While most cyberattacks come from outside sources, an increasing number involve an organization’s own employees.
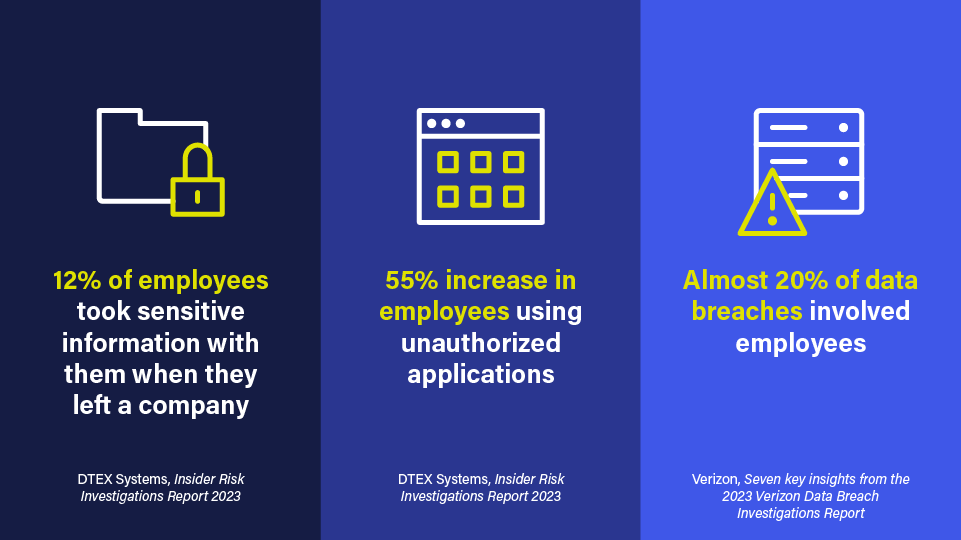
A 2022 study found that 12% of employees took sensitive information with them when they left a company. The same study found a 55% increase in unauthorized application use, with employees who weren’t supposed to touch certain apps using them anyway. Another major study found that almost 20% of data breaches involved “internal actors”—generally employees misusing data either intentionally or unintentionally.
You probably trust your employees, but you also need to take precautions. Staffers should see only the information they need to see and use only the apps they absolutely need to use. Plus, your firm should be able to track exactly who has used which apps, worked in which files and when. All of that would likely be part of the SEC’s new reporting requirements, but it’s also just good security practice.
With a document management app running the cloud, you can do all of that. You can see who has accessed what and when, and you can restrict access to specific applications and client files. It might seem like a draconian measure, but it’s simply smart management of both security and employees. Taking precautions isn’t just about guarding against employee theft. It’s also about protecting your data from honest mistakes.
Accounting cybersecurity: From Washington with love
Your firm might not have to deal with the SEC or any companies registered with the SEC, but new government regulations coming from such a high level are worth following. If nothing else, they should serve as a reminder that accounting cybersecurity is always paramount. If you can’t summarize your security strategy, try rethinking it. Your firm is safer in the cloud. Move there today.


