The Dark Web—What is It?
The deep, dark web—what is it? What’s it used for? How does information end up there? And what should you do if your information is found there?
In this post, I’ll be diving into all the above. Let’s jump straight in.
Fact #1: The Deep Web and Dark Web Are Two Different Things.
First off: Let’s set the record straight. The deep web and the dark web are two different things.
The internet is comprised of three different “sections;” the surface web, deep web and dark web.
The surface web is what is searchable and indexed by sites like Google and Bing.
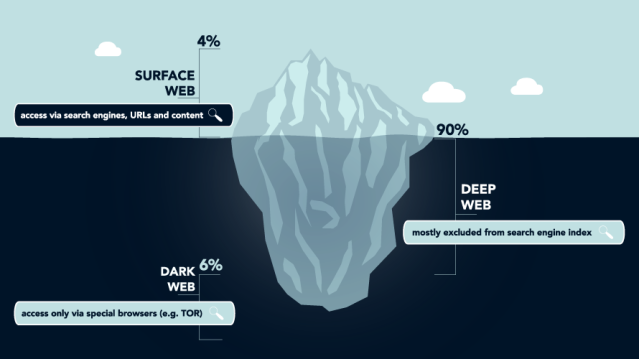
The deep web “refers to anything on the internet that is not indexed by and, therefore, accessible via a search engine.” (CSO Online) It includes paywall-only content and content that requires sign-in credentials, like medical records, membership websites and confidential corporate web pages.
Much of the internet is comprised of the deep web.
The dark web is a vastly different, primarily nefarious subset of the deep web. Although not all the dark web is used for illegal purposes, it is known as the birth date, social security and bank account number marketplace…which brings us to fact #2.
Fact #2: The Dark Web is Where Criminals Can Go to Buy, Sell and Trade Stolen Credentials.
Let me tell you a quick story:
I’ve personally had my credit card number stolen. Years ago, before I did much (if any) online shopping, I noticed a few transactions hit my account. The transactions were all New York City-based. (I live in the middle-of-nowhere New Hampshire.) The charges were for small amounts at a well-known fast-food restaurant. (Charging small amounts to see if the legitimate owner notices is a well-known tactic. The criminal’s thought process is, “If they don’t notice these transactions, they most likely won’t notice incrementally larger amounts…and I’ll be able to use the card for longer.”)
I immediately called my bank, notified them that my credit card number had been stolen and canceled my card.
How did it happen? My credit card was still in my wallet; I didn’t have more than one copy of it. I hypothesize that my credit card information was picked up via scanner while I was in a public place, then sold on the dark web.
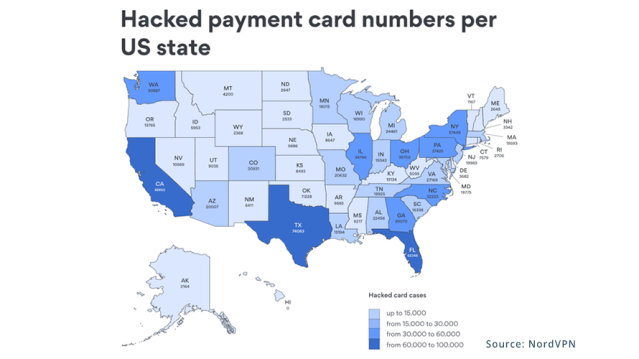
It’s easy enough to purchase a credit card scanner. (For this blog post, I searched “credit card scanner” and found several surface web websites selling them.) In the U.S. alone, there are “1.6 million card numbers for sale.” (pcmag.com)
Fact #3: It’s Impossible to Guarantee that Your Information Will Stay Off the Dark Web.
Unfortunately, there’s no definitive method to prevent your information from getting onto the dark web, but that doesn’t mean you can’t try.
Anyone who browses online must know how to protect themselves from the dark web.
As individuals, we must protect our personal information from getting misused online. But it’s just as essential to ensure our work credentials aren’t getting traded around on the dark web.
To ensure your information remains private, here are a few things you can do to protect yourself from having your information leaked on the dark web:
- Never email sensitive information: If you must share your social security, credit card or bank account number, do so in person or over the phone. And before you do, ask yourself: Do I know the individual asking? Do I trust this institution? Don’t be afraid to ask questions about the intended use. It’s YOUR information, after all.
- Practice good password hygiene: Don’t share passwords, don’t reuse passwords and change passwords often. Get more practical password hygiene tips here.
- Don’t visit or buy things from unsecured sites: Unsecured sites are sites without the “s” at the end of http. Always check to ensure the sites you visit contain that “s” (https:) or secure socket layer (SSL). The SSL certificate helps secure information such as login credentials, credit card transactions, bank account information and much more.
- Use multi-factor authentication: Multi-factor authentication verifies your identity post-login and pre-access. This means that even if your credentials are stolen, the perpetrator wouldn’t be able to gain entry into the program they’re trying to access. Instead, you would get a notification (usually via phone) that asks you if you are trying to log in—if you’re not, you click “deny,” blocking the intruder from entering. Learn more about multi-factor authentication.
Fact #4: You Can Monitor Whether Your Information is Located on the Dark Web.
Okay, so we’ve learned that it’s near impossible to keep your information from ending up on the dark web. We’ve also learned that there are ways to protect yourself…but nothing is guaranteed.
So…what can be done?
Luckily, there are ways to determine if your information is on the dark web. Products like Right Networks’ Security Awareness Training provide a service called dark web monitoring.
Not all dark web monitoring services are built the same, but Right Networks’ monitoring continuously scans the dark web for illicit activity involving your brand 24x7x365.
Here’s how it works. You work for XYZ Accounting Firm and use the domain @xyzcpas. One day, your email address and password appear for sale on a dark web website. Right Networks is alerted, and then you are, too.
Dark web monitoring is essential because it protects your brand from being sabotaged by malicious individuals.
Think back to the personal example I provided in the buying and selling stolen credentials section.
What if it had been my QuickBooks® login credentials rather than my personal credit card information? In one fell swoop, the buyer of my credentials would have access to my entire book of business, including their customers’ contact information and financial data.
Learn more about dark web monitoring and Security Awareness Training.
Fact #5: There Are Steps to Take After Your Data is Found on the Dark Web.
Lastly, you can do a few things if your information is on the dark web. Your exact actions will depend on the specific information found, but it’s safe to say that practicing all of these steps for all of your accounts is a good idea:
- Change your passwords.
- Use multi-factor authentication.
- Comb through your recent debit card and credit card transactions.
- Notify your credit/debit card provider if any transaction seems suspect (and request a new credit card).
Beyond these steps, it is your responsibility to be proactive about your data privacy and security. Invest in a security awareness training program. Install local machine security services. Begin working from cloud-hosted programs.
And always remember that at Right Networks, we offer all of these solutions to help businesses like yours stay secure.
For more security information, visit us at rightnetworks.com/cybersecurity-solutions.



